Widgetized Section
Go to Admin » Appearance » Widgets » and move Gabfire Widget: Social into that MastheadOverlay zone
Bring Your Own Identity, The Next Big Thing
The views expressed are those of the author and do not necessarily reflect the views of ASPA as an organization.
By Iriana Chizek
Organizations are continuously trying to enhance the users’ experience by allowing them the capability to merge both their business and personal identity. This can be done using existing business and personal devices without the need for multiple logins or additional credentials, thus giving rise to concept of “Bring Your Own Identity” (BYOID). BYOID is a method by which users can digitally authenticate to an organization with credentials that are managed by a third party. The third party assumes the privacy and security liability of traditional identity access management (IAM) systems. However, the organization will still maintain the IAM related to user rights. Think for example, when a website allows a user to login using their credentials to an existing social site such as Google+, or ‘social login’, without having to create a new user name and password. Simply put, BYOID means enhancing the user experience and enabling users to log into multiple sites without the need to remember multiple login IDs and passwords. This paradigm reduces user overload by creating a seamless connection and providing a positive customer experience.
Organizations need to keep up with the technology demands and their users, while delivering world-class service and without sacrificing security. Information technology (IT) professionals and organizations have become increasingly aware of the risks and rewards when it comes to adopting BYOID. In a recent survey conducted by Ponemon Institute and CA Technologies, ‘34 percent of information technology users say risk/liability concerns followed by complexity (21 percent) and loss of control (19 percent) are barriers to deployment.’ So, does the convenience outweigh the cost of privacy and security of the users’ information?
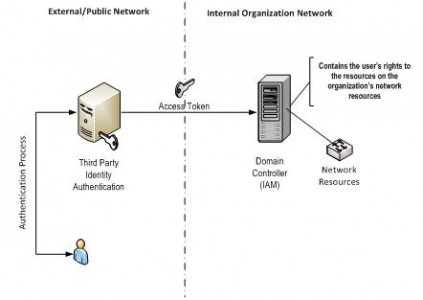
To understand why BYOID is secure, a more technical discussion would need to be undertaken. BYOID is less about authentication and more about delegated identity management (authentication) to the organization’s system. Under BYOID, the user makes use of a third party for identity authentication. Through secure means, the third party sends an “access token” to the organization’s “login or domain server.” The domain server is managed by the organization. The domain server has the user’s rights to the resources on the organization’s systems. This allows the organization to maintain control over its user’s access and thus balance its risks related to security. The diagram presents how the user authenticates via the third party and obtains their access rights via the internal organization’s domain controller.
One of the main security concerns that would come into play would be the cascading effect that ensues on all shared sites (including the organization’s) should the user’s password and login ID become compromised. This concern becomes more tempered as users become more guarded about their identity. Moreover, this reinforces the need for organizations to be proactive and educate users about information security. The security awareness training provided by the organization should instruct the users on:
- Properly safeguarding login credentials.
- Physical security related to their devices.
- Organizational data and confidentiality requirements.
An additional benefit of outsourcing identity authentication is the ability to add another authentication step for multi-factor authentication. Multi-factor authentication requires the user enter at least two forms of data thus increasing security and reducing the risk of compromised logins. While the addition of multi-factor authentication by an organization can be complex and costly, outsourcing it makes the implementation easier and becomes a pay-as-you-go exercise without the addition of the expensive equipment and software.
One of the arguments for BYOID is that users could have one authentication point for their work login as well as their bank, investment accounts, Google, Facebook or Twitter. The issue arising from this is related to organizational boundaries and the intermingling of personal and professional information. Under this paradigm, authentication is segregated from user rights. So the concern is more psychological than it is related to organizational boundaries.
BYOID is here to stay. In order for it to be successful, organizations must develop discussions between information technology professionals, stakeholders and operational management. These discussions should center on risk and reward of adopting BYOID, while considering the following:
- Readiness of internal domain servers to accept third party tokens.
- Development of processes to de-couple user role privileges from the authentication process.
- Potential third party providers identified should follow at least one security framework, such as that provided by the Cloud Security Alliance (https://cloudsecurityalliance.org/star/).
- Security service level agreement requirements for potential third party providers related to data protection, data manageability and data security requirements.
- Implementation of security awareness (components) training for users.
Author: Iriana Arias-Chizek is a manager at Lurie Besikof Lapidus & Company, LLP. She can be reached at [email protected].


 (2 votes, average: 4.50 out of 5)
(2 votes, average: 4.50 out of 5)
Follow Us!